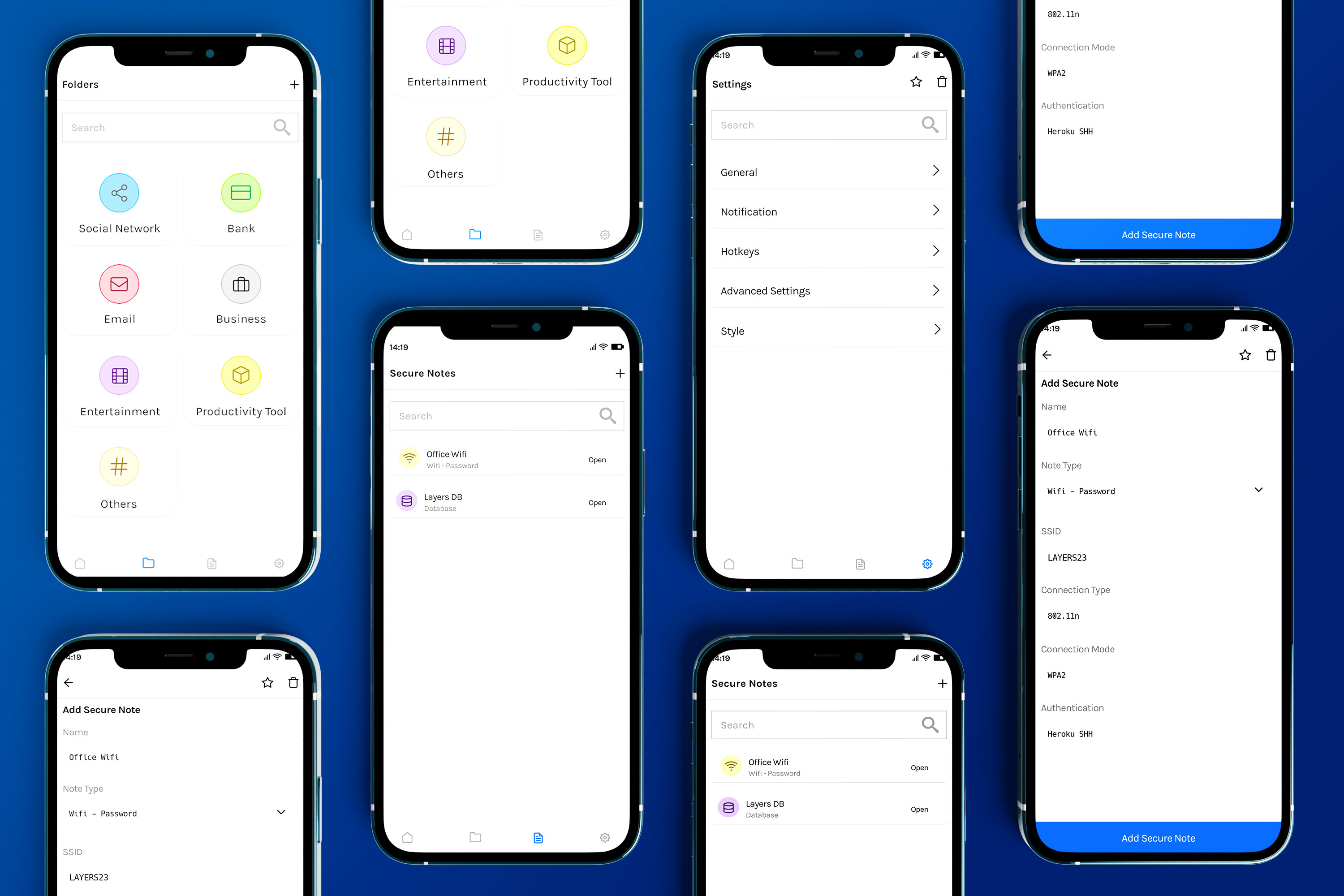
Portfolio
Secure Keyboard Solution


StrikeForce Technologies is the world’s leading provider of Mobile Security Solutions. They sought the assistance of AllianceTek to port remake their existing application ‘ID Genie’ with new enhanced security features and cross-platform capability. AllianceTek developed the application with the six most powerful security features that every enterprise mobile user must have to maximize security and consolidate their digital identities. This allowed StrikeForce to explore new revenue channels while providing a more robust service to their existing customer base.
Opened doors for new revenue channel because of cross-platform solution that can be accessed by other mobile device users.
The client received an enhanced security application.
Loyal user base due to easy migration of licensing when they change their device.
As an IT partner and solutions provider, AllianceTek will help you follow your objective and implement strategies that are unique to your business to see it through to completion
AllianceTek designed and developed altogether a new keyboard SDK to create a custom encrypted keyboard for Android and iOS apps which can encrypt all keystrokes between on-screen keyboard and browser.
Offered improved user accessibility, usability and security with SSL integration.
A unique licensing feature was introduced that allows the user to move the license from old device to new.
Independent and single tap solution to manage mobile security.
AllianceTek performed an in-depth research in providing this cross-platform security solution.
Fully encrypted keypad functionality to enable them to achieve complete security against key-logging traits.
Reduced hierarchical hassles for encryption/decryption as the system follows minimum access rights.